Hacknoid Pro
Manage your Vulnerabilities in an Automated and Simple Way


Hacknoid PRO
Tired of Complex Tools and Reading Endless Reports?
That’s why we bring an automatic detection of vulnerabilities in all your devices, alerting through a simplified and comprehensive dashboard of all the alerts that exist and being able to access a battery of reports instantly where to visualize, prioritize, have details of each vulnerability, statistics and summaries of the evolution of the treatment of vulnerabilities over time.
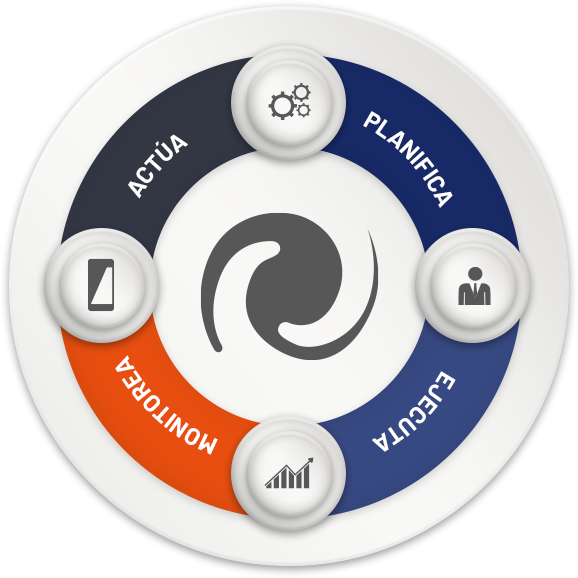
Leading Cybersecurity Management Software
Continuous Vulnerability Assessment
VISIBILITY
Automatically discover your assets and test all known vulnerabilities for each
MINIMIZE EXPOSURE TIME
Threats are highly dependent on the time they remain active. Early visualization and action will reduce these gaps
COMPREHENSIVE VISUALIZATION
Simple and prioritized vision. Hacknoid allows you to model your organization and see it thoroughly to make efficient decisions and support the resolution team
EVOLUTION REPORTS
You will be able to see how cybersecurity is evolving by extracting customized reports and presenting them to the responsible executives
SUPPORT IN THE MANAGEMENT OF STANDARDS AND BEST PRACTICES
Hacknoid allows you to update your inventory, group by criticality, business area, and owners
Cybersecurity Dashboard
Comprehensive visibility of what's happening in security issues
CONFIGURABLE WIDGET
Configurable by user Groups the most critical systems and monitors those elements with greater frequency and control
INDICATORS AND PROCESS VIEW
Color by criticality Indicator of the number of alerts
ALERTS AND AGENDAS
Classification by type of alert and degree of criticality describes alert characteristics and gives solutions details
WEB SCANNING
Scanning of a domain from the outside, pretending to be a cybercriminal





